In this article, we look at the top 5 network security best practices that all businesses should be following.
#1 – Install a Unified Threat Management (UTM) appliance to improve your network security at the edge
Install a Unified Threat Management (UTM) appliance that supports most or all of the following features: content/malware filtering, website filtering, application filtering, spam filtering, and one that provides VPN access for mobile users.
Some of the most popular appliances we recommend and support include products from Cisco, Fortinet, Lightwave, Sonicwall, Sophos, and Untangle. These devices act as your company network’s first line of defense and minimize your company’s attack surface to-and-from the internet. You can carve-out a large fraction of unneeded internet resources (known malware sites and time-wasting websites) to entire countries via GeoIP filtering which helps lower IT support costs and increase your end-users productivity.
UTM appliance vendors have a large range of hardware and feature-sets to choose from and can support small business networks (fewer than 10 end-users) up to large enterprise environments with several thousands of end-users.

This Wisconsin manufacturer needed to modernize its IT infrastructure to support rapid business growth.
Discover what they did#2 – Keep your security appliances, servers, and clients updated with the latest security patches

In medium and large Windows environments we recommend incorporating Windows Server Update Services (WSUS) to deploy and report on client’s and server’s update history. For smaller environments, local group policies can be used to enforce Windows update policies. In both situation, I typically recommend rolling out and installing updates at Noon on the Friday following patch Tuesday for all client systems.
Server updates, on the other hand, are commonly published and manually installed during regular server maintenance cycles. Security appliances such as UTM’s, firewalls, and networking equipment should always be updated with their latest “stable” firmware. This includes signing up for security advisory email alerts for the products you own so “you’re in the know” when security patches are released.
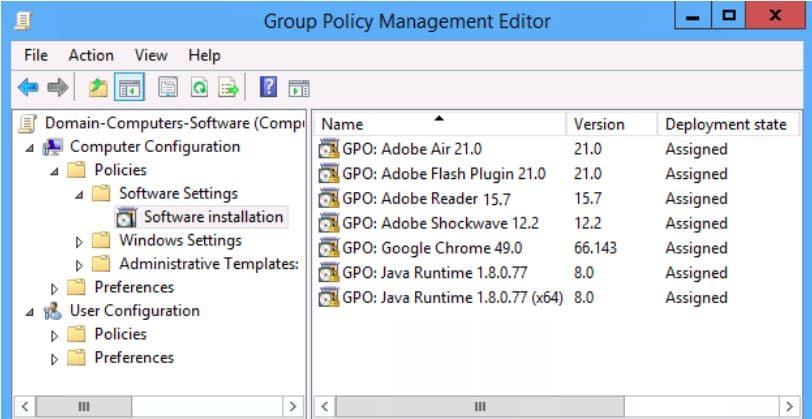
#3 – Implement a software deployment strategy for 3rd party security updates
Many critical security updates can be easily rolled-out out to your client computers through Active Directory services or other software deployment methods. Outdated Adobe and Java installations are two of the most commonly exploited software add-ons that open the doors and can make your systems vulnerable.
Of course, this won’t guard against zero-day exploits, but it will limit your footprint against the script-kiddy hackers that are determined to find the right tools to run a dictionary of exploits against some of your most critical systems.
#4 – Do not use administrator accounts for daily work
I still see this problem in nearly every new environment I step into, and I personally think that this is the number one problem that costs companies money and lost productivity. Back in the Windows XP days, it was a headache to administer end-users that only had domain users and power users memberships (but it wasn’t impossible – I was there). In certain situations, it was common to use products like Deep Freeze that froze the state of your computer so it could easily be restored to its optimal state after a simple reboot.
The tides have changed many years ago, and the team at Microsoft made huge improvements to their Windows operating systems. All your local end-users, yes, including your account and the president’s account” should not have the ability to install software or make system changes. This problem is easily rectified by having another designated local admin account, or a domain group that can be used by you and your power users when they need to gain higher access and privileges to their system.
Again, the purpose here is about limiting your attack surface and adhering to the old adage of “principle of least privilege”. If your account, or the president’s account, is compromised, the company will be better off and less susceptible to potential damages if those accounts do not have administrative-level rights.
#5 – Backups, backups, and more backups – onsite, remote onsite, and offsite
Along with all the other items in this article, backups are still, without any doubt, the must-have safety net for your network. Along with a good backup strategy that meets your IT demands, backups that are reliable and accessible are critical. You, or your IT vendor, should also be using commonsense, for example, re-locating your NAS backup device(s) from your main closet to a remote closet (if possible), or even better, moving it to a remote building. This can quickly provide an instant, semi-offsite backup strategy for your company’s data.
The possibilities for improving overall network security are endless!
Any experienced network administrator will tell you that there is an infinite range of security when it comes to your network. Along with these Top 5 items, it should be noted that strong passwords, encryption, end-user due diligence, and basic common sense (let’s not forget that one!) should be incorporated into your security goals and initiatives.
Keep in mind, these Top 5 items and concepts are very easy to implement and should be considered standard, best practices, for improving overall network security in your organization. It doesn’t even take a lot of time, resources, or costs to implement them properly, and it may one day save your company from cyber threats and potential disaster.




