For a long time, a cyber attack seemed to be a problem that only affected the largest multi-billion dollar corporations. But as these organizations have strengthened computer security, criminals have changed tactics.
Taking on a bank could net millions of dollars for instance, but the level of planning and resources required to break through network security is substantial. As a result, many criminal gangs now target smaller businesses who tend to have weaker defenses. They may need to complete more cyber attacks, but the level of effort required tends to be much lower.
This places businesses of all sizes at risk of cyber attack. Here are six practical steps you can take to improve your computer security.
#1: Train your staff (regularly)
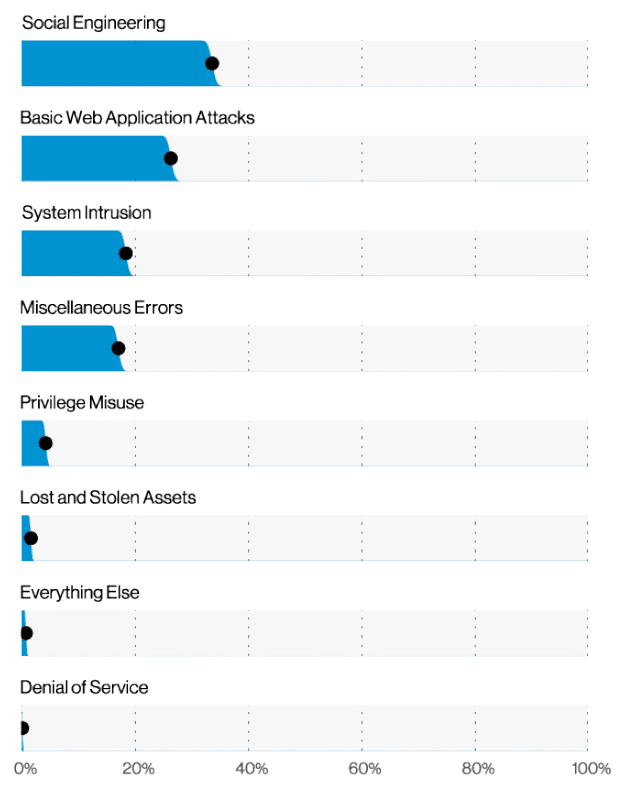
Hackers get the blame for most network security breaches – but the reality is most incidents start much closer to home. According to Verizon’s Data Breach Investigations Report for 2021, the most common source of network security breaches is social engineering attacks; 35% of successful attacks rely on simply tricking your users into divulging their credentials.

This Wisconsin manufacturer needed to modernize its IT infrastructure to support rapid business growth.
Discover what they didPhishing emails, infected email attachments or simply asking users for their password, hackers have a range of simple, effective techniques that give them access to your IT systems. And these tricks work because your employees are not prepared – or able – to spot social engineering attacks.
Training staff to identify potential threats and take greater responsibility doesn’t have to be a major undertaking.
For end users you may find a basic, free resource like the CISA Cyber Essentials is just detailed enough to help everyone play their part in improving computer security.
For greater protection, your IT team may benefit from working with a specialist to conduct an assessment and develop a security awareness plan that helps build skills in-house.
#2: Reinforce login security
According to Verizon, the second most common cyber attack is the basic web application attack. This sees cybercriminals attempting to break into your web-based systems to steal money, compromise your IT systems or to simply deface websites.
These cyber attacks are very basic, but quite effective. Hackers will use automated tools to test hundreds of thousands of usernames and passwords until they find a combination that allows them access. In many cases these attacks rely on the bad security habits of your users and customers – particularly recycled passwords. Using credentials stolen from other websites, hackers will test the same passwords to see if they also work on your systems. Because many users choose the same passwords repeatedly, this technique is very effective.
The key to preventing these attacks is to boost login security using some basic cybersecurity solutions. You should consider:
- Multi-factor authentication (MFA) – To login, users will need to supply their user name, password and a third piece of information, such as a code that is sent to their mobile phone. This minimizes issues with reused passwords because hackers cannot access the additional detail. Learn more about MFA types.
- Limit logon attempts – By automatically locking accounts after a set number of attempts, you can block the automated tools used by hackers. For completeness, you should implement similar limits on your internal systems too. Microsoft has some useful guidance on this.
- Use CAPTCHA – An alternative to MFA, CAPTCHA requires users to perform a ‘test’ before they can log in. The system generates a picture that the user must decipher (like obscured text) – automated systems typically lack this capability. Google has a handy guide about how the system works.
#3: Boost internal monitoring
It is a sad fact that a percentage of cyber attacks originate inside the corporate network. Whether through malicious activity or negligence, your own staff can compromise network security and cause as much damage as hackers.
Preventing these issues relies on being able to detect what is happening inside the network. Which is why an effective computer security strategy needs to look inwards as well as out.
To avoid future issues you will need to implement internal monitoring that can alert you to suspicious activity. You can also audit activity to trace who has done what – and to better understand how to reverse any damage caused. Most applications include logging tools, so it is simply a case of enabling the relevant settings – and dedicating time to regularly review activity to spot problems earlier.
Microsoft offers a short online training module to help you better understand system security.
#4: Deploy endpoint security
Every device connected to your network presents a potential attack point for criminals. As more people are working from home, the number of entry points to your network has increased substantially.
Protecting every device connected to your network – PC, notebook, tablet, smartphone etc – is critical. Endpoint security tools like antivirus software will prevent hackers from installing malware or ransomware – and reduce opportunities for them to gain a foothold inside your network.
Anti-malware tools are relatively inexpensive and easy to install. If your in-house team lacks the resources or experience, a third party endpoint security service can help bring your endpoints under control.
#5: Prepare for the worst
Experts are agreed that businesses should adopt a “when not if” approach to cyber attacks. This means you should assume that your computer security will eventually be breached – and that you need a plan to restore lost data and systems as quickly as possible.
Disaster recovery (DR) plans are not just for dealing with fires and earthquakes – they are also intended to help you resume operations quickly after a cyber attack or ransomware infection. The plan should help you mitigate any kind of computer security incident as required.
It takes time to formulate an effective DR strategy, but you can make a start now. Ensuring your core systems are being backed up and can be recovered is absolutely essential to protecting your business. You should check that this most basic requirement is in place immediately.
Again, Microsoft offers a useful training course for your IT staff to help them understand and implement disaster recovery techniques.
Overwhelmed?
As your IT systems develop, they also become more complex. Many smaller organizations lack the skills and experience to properly understand network security – particularly as they work so closely with the systems every day. This is where a cybersecurity assessment from a trusted and reliable IT partner comes into play.
To be valuable, a cybersecurity assessment should have three parts:
#1: Where are we?
A cybersecurity assessment will help you understand the current status of your defenses against cyber attack. Expert computer security consultants will evaluate your systems to identify what is, and is not, working correctly so you have a baseline understanding against which to improve.
#2: What do we need to do NOW?
The cybersecurity assessment then provides an action plan to highlight the issues that require immediate attention. All other potential issues are then prioritized by risk and severity so you can allocate resources to achieve an industry-standard level of network security.
#3: Where are we going in future?
Your IT systems are continuously evolving, so you need a longer-term strategy that will grow and flex accordingly. The plan should outline future investments in cybersecurity solutions – and the resources and people you will need.
Using the assessment, you can make strategic decisions about tasks and capabilities. Which should be kept in-house, and which should be handled by specialist partners? Asking – and answering – these sorts of questions will help you better plan the budgets and partnerships you need to reach your strategic goals and better prevent cyber attacks.
For organizations in Wisconsin, Source One Technology provides a cybersecurity assessment that looks at your firewall, email, backups, endpoints, policies and employee awareness. Protect your business, data and staff today!




