With many organizations choosing to move services to the cloud, the difficulty for most is related to the overall Security within the Cloud. If you are using Office 365 for services such as Email, Instant Message, Collaboration, File Storage or even as a fully-fledged cloud Phone System, Microsoft provides multiple components to ensure the Office 365 tenant ( i.e. your data) is secure, but you as the organization need to license and enable them.
Usually, organizations don’t migrate entirely to the cloud, as on-premises applications are often required. During the migration process to Office 365, a Hybrid design if often utilized allowing for a mixture of cloud and on-premises tools and applications.
To truly secure an Office 365 tenant, you first need to understand how all of the services communicate and what is available out of the box. You will also need to know how to protect the network traffic coming from the on-premises network to the tenant.
Office 365 perimeter protection
A core focal point for all organizational IT infrastructure is the protection at the edge. Historically, companies spend most of the money on edge protections such as routers, content inspection platforms, and firewalls. The advantage of moving to the cloud is the near-elimination of these devices and platforms, due to the nature of it being in the cloud and managed by a provider. However, just because you migrate to the cloud, does not mean you have inherent security. You still need to protect network traffic that flows between your on-premises network and the cloud, as well as external direct traffic.

This Wisconsin manufacturer needed to modernize its IT infrastructure to support rapid business growth.
Discover what they didThere are multiple options to protect the edge, from standard network appliances, software, and hardware. The goal is to control how users get to the cloud service itself. Office 365 supports controlling access to an Office 365 tenant for example via Internet Protocol (IP) Address blocking. This is basically blocking at the lowest level and ensuring that only IP ranges that are company protected can gain access. For example, within Azure Active Directory you can set the IP address ranges that map to specific locations, allowing you to control IP access.
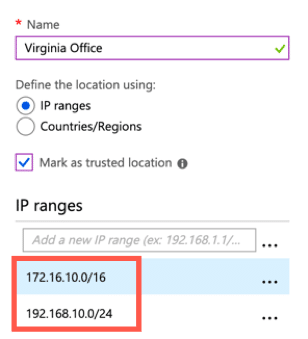
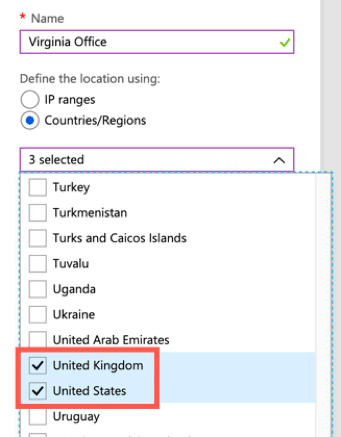
Conditional access policies can also be enabled ensuring that geo-locations are respected, and only approved locations can connect. Locations can also be set to specific countries within the same conditional access policies instead of using IP address ranges. In this example, the location named “Virginia Office” allows connections only from the United Kingdom, the United States, and Germany.
In fact, when creating the policies itself, you can determine whether to “allow” or “block” locations as needed. You can set the control within the conditional access policy using “Access Controls” and choosing either option. You can then specify the criteria such as locations.
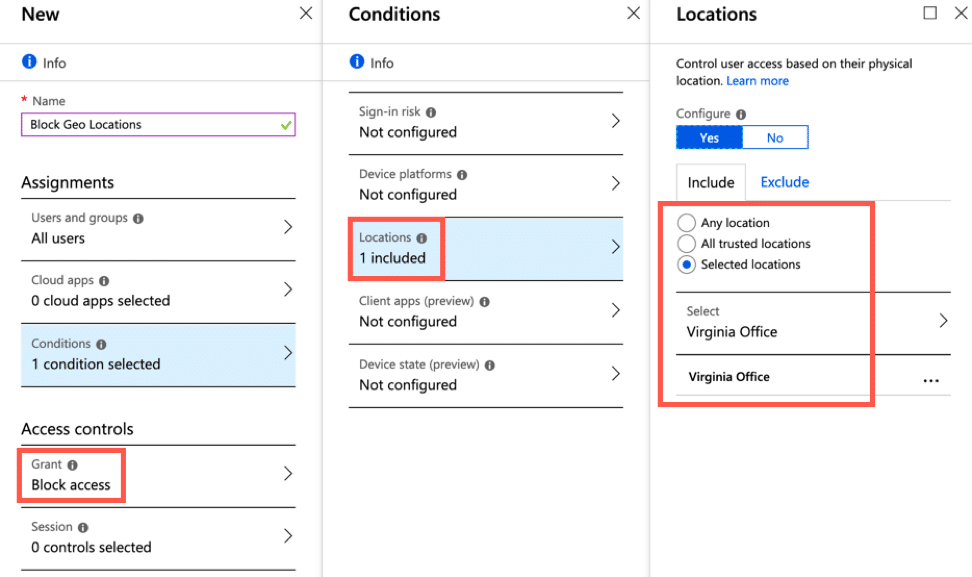
Controlling the door to the cloud is imperative to ensure that only those you trust as users can access the services as needed.
Authentication protections
A barrier to collaboration on-premises is always authentication. Compared to the cloud, it is much harder for users to simply gain access to an internal application or service hosted within the corporate network. Authentication tends to be strictly controlled through for example Active Directory, or another directory platform, which is not made available externally at all.
The Office 365 tenant login experience is designed using industry standards for authentication which makes this process simpler and enterprise ready. However, for the cloud, the whole premise of this is to share and make external collaboration easier, so end users can easily share content and allow non-organizational users to access content. Office 365 does, however, support different sets of external sharing capabilities. Accessing the Sharing settings within the SharePoint Administration site, allows you to set the direction of allowed sharing, plus who can be shared with. For example, the default settings (shown below) is set to allow sharing to authenticated users plus utilize anonymous links.
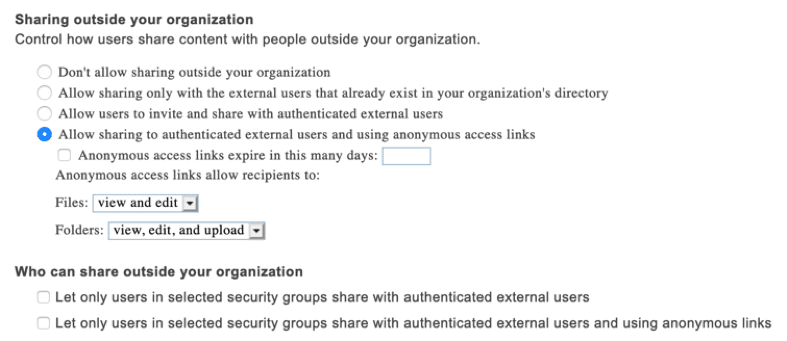
Defining external sharing policies will allow you to control how and when external users are able to access content shared with them. Links can also be sent to external users that expire after specific dates as well as being limited to what the end user can do with the content. Once the settings have been defined in the administration consoles, for either SharePoint Online or OneDrive for Business, the end user experience allows for more granular control over sharing, for example allowing anyone with the link to the document to have access and even edit.
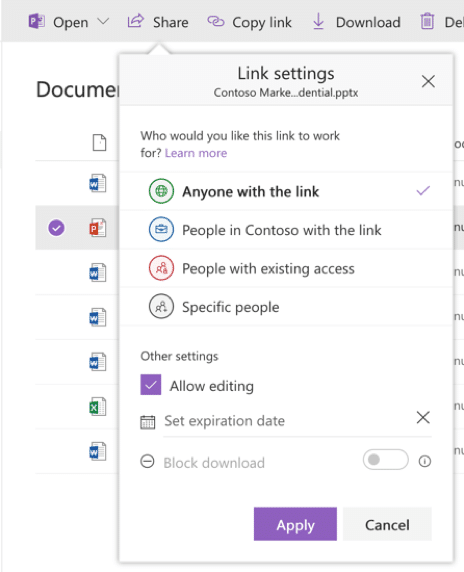
These controls allow end users to still collaborate but within the boundaries defined by the organization. This approach provides for protections as collaboration is performed within or without the organization.
Content and data controls
Knowing where your content is, and how to secure it, is always a critical problem for many organizations. Moving to a collaboration platform such as SharePoint Online or OneDrive for Business, makes many organizations nervous due to the collaborative nature of the services. Many companies store Personally Identifiable Data (PII) within SharePoint. As such, knowing which security controls and functions to use for this type of content is now more critical than ever.
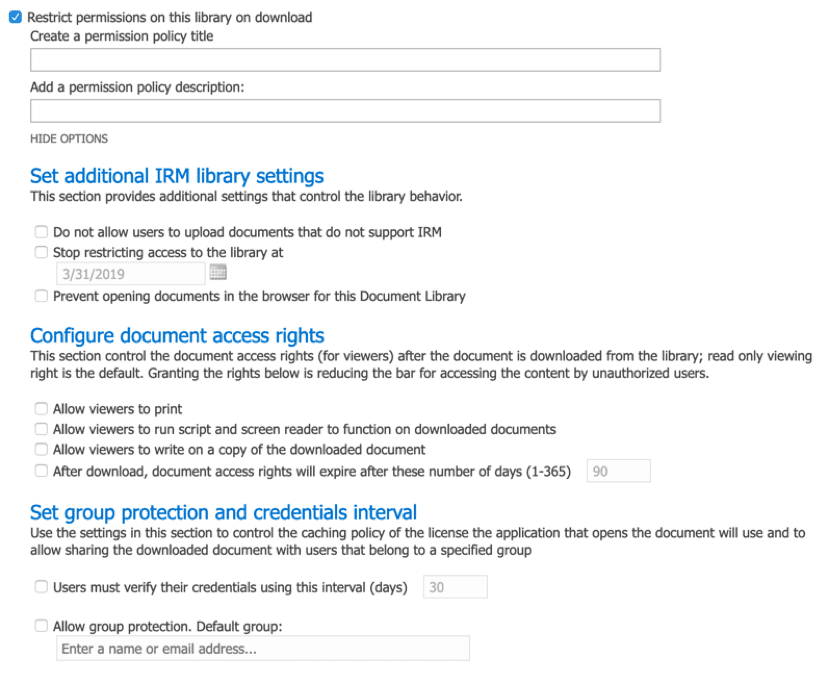
SharePoint Online supports Information Management policies that provide the ability to control what happens to the content over and above the base permissions. These policies can restrict for example end users from copying and printing the material. Information Management policies go hand in hand with permissions, allowing almost less structured permissions, knowing that the policy will always be over the top of the permissions sets.
These policies work through the use of Information Rights Management (IRM) services which is part of Office 365. It can be activated directly through the SharePoint administration interface. To enable Information Rights Management (IRM) within a tenant, navigate into the SharePoint Administration site, and set the following option. This will then enable the settings within the site collections allowing policies to be defined with libraries.

Policies can then be created within document libraries and applied to the content as needed. To access the policy options, navigate into the document library of choice, access the library settings and choose the Information Management option, which will then allow you to set any of the following properties for policies that will apply to documents stored within the library.
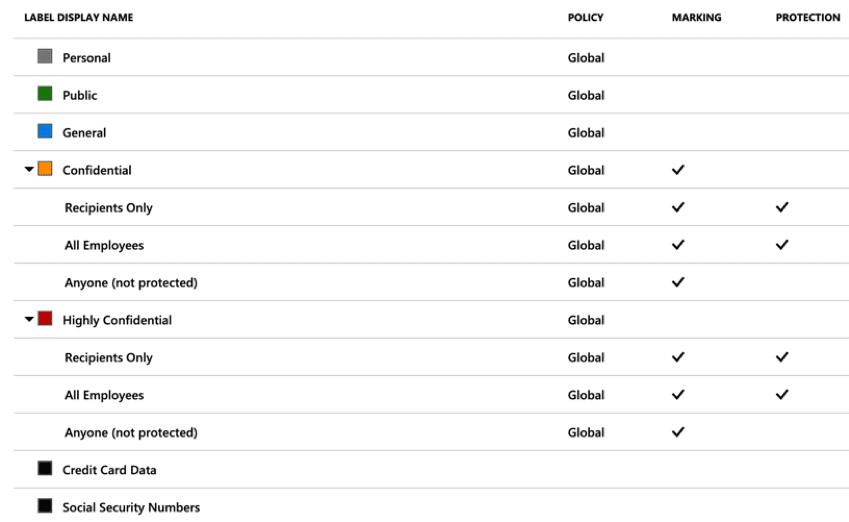
To enhance this further, Microsoft provides a service called “Azure Information Protection (AIP),” that goes above and beyond Information Rights Management policies. These policies exist with the parent service Azure, and once applied to the content stay with it, no matter where it then resides. Within “Azure Information Protection” all of the labels and associated policies are listed.
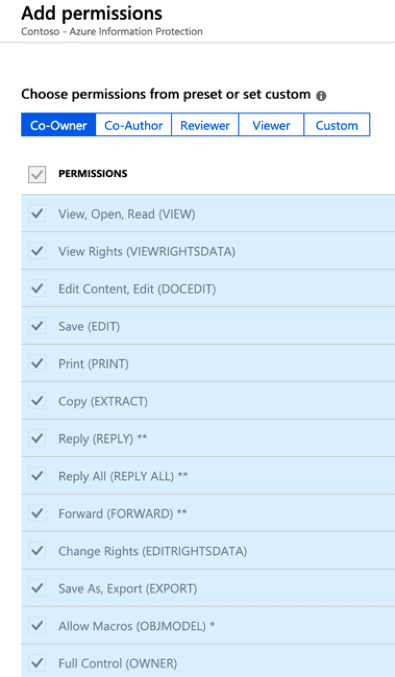
Each policy contains restrictions that will be applied to the content, controlling what happens to it as it moves around the Office 365 Tenant or other locations. Clicking into a label policy allows you to set the permissions on a role basis such as “Co-Owner“, “Co-Author“, “Reviewer“, “Viewer” and then custom permissions as needed.
These policies work well and protect content as it moves around the company. However, another service that can control the flow of content based on templates and policies is Data Loss Prevention. Data Loss Prevention (DLP) rules, can block content from being accessed as well as limit its flow either within the organization or outside. DLP support not only SharePoint Online but also OneDrive for Business and Exchange, with support coming for other services within Office 365. The criteria for a DLP policy can be based on any number of sensitive types, which are then set in the “Find content that contains” section of the policy.
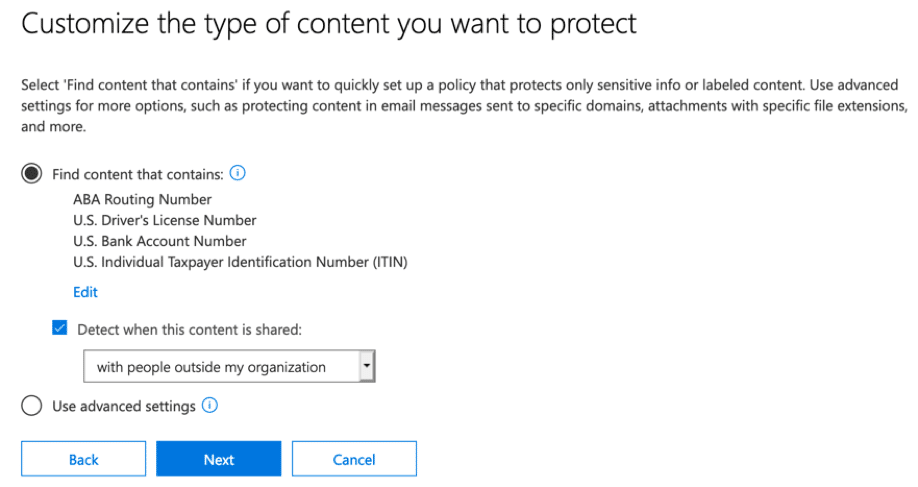
Mobile Access Control and policies
Office 365 provides two mobile device management capabilities. The first is Mobile Device Management for Office 365 (MDM), and the second is Microsoft Intune. Mobile Device Management for Office 365 offers simple yet powerful protections for any device that connects to services within Office 365, such as Exchange Online, OneDrive for Business and SharePoint Online. These policies modify and restrict devices, ensuring they meet the criteria you decide as an organization. Password and passcode protections assure that devices are secure before connecting to a service.
Along with standard device protections, encryption can be enforced ensuring that all content is protected and controlled by the organization. By defining a policy for mobile devices, all service access is checked and blocked as required. Utilizing the MDM capabilities will allow you to set Office 365 tenant restrictions for any device that connects. When Mobile Device Management for Office 365 is coupled with service protections found within OneDrive for Business and SharePoint Online, connections can be controlled by network address as well as restricted to organization managed devices. Clicking into the OneDrive for Business Administration site, allows you to navigate to the Device Access section, then enable a standard policy for mobile devices.
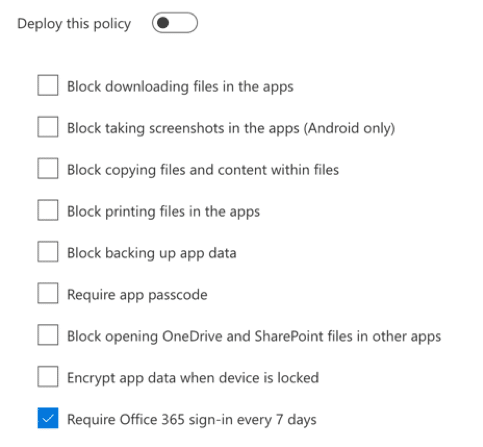
Microsoft Intune adds further capabilities to mobile device management. As a fully-fledged MDM, every aspect of the mobile device can potentially be modified to ensure that a managed device is controlled and secure. With unmanaged or personal devices, enhanced policies plus conditional access controls can assure devices only connect to Office 365 services when they are granted the right access and meet the requirements of your security controls.
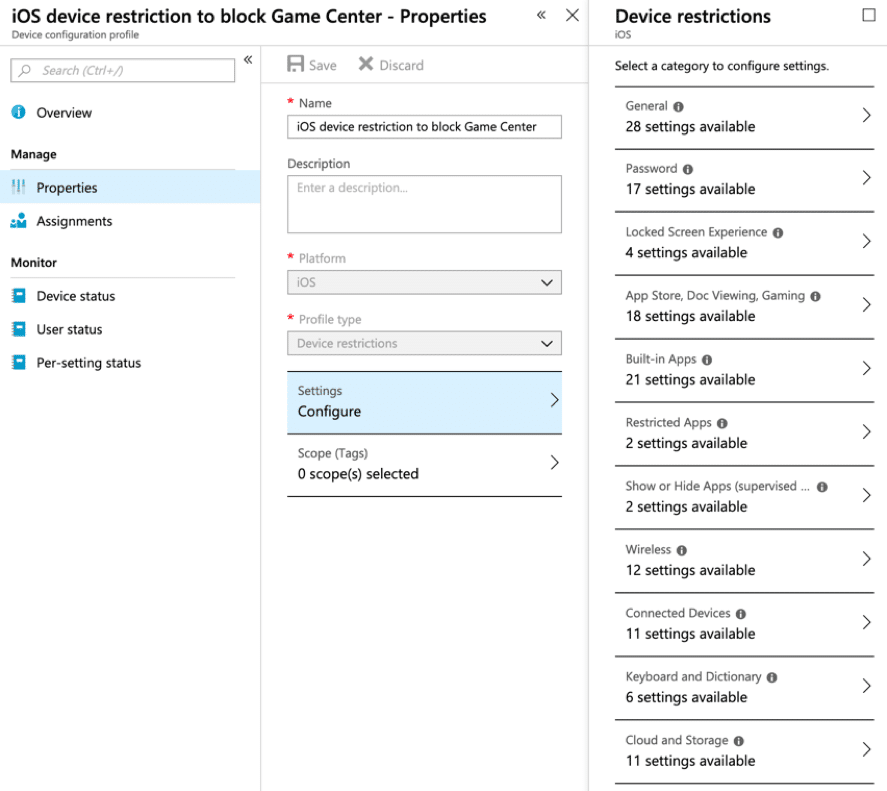
Microsoft Intune allows more granular controls such as controlling applications and services directly within the device. Creating a new policy for example that can block the “Game Center” within an iOS device is as simple as setting it to restrict in the policy.
Recommendations
As with any IT solution, enabling the right components and services is critical to its security. As an organization chooses to migrate to Office 365, a plan for rollout needs creating and implementing. As part of this plan, a governance committee controls the implementation of all end-user, administration and security features. This will ensure that only those features that the organization is ready for are implemented. Too often, companies spend too much time implementing new features, that have nothing to do with Security, which can lead to problems and issues in the event of a data or security breach.
As an organization, review the current licenses for Microsoft 365 (Azure and Office 365) and ensure that the required Security licenses are purchased along with enabling the correct features.




